权限服务
基础环境搭建
在开发权限服务的业务功能之前,我们需要进行基础环境的搭建,这是权限服务的基础。这些基础环境包括:配置文件、配置类、启动类等。
配置文件
bootstrap.yml
由于我们当前使用的是Nacos作为整个项目的配置中心,所以Spring Boot的大部分配置文件都在Nacos中进行统一配置,我们的项目中只需要按照Spring Boot的要求在resources目录下提供bootstrap.yml配置文件即可,文件内容如下:
bootstrap.yml的加载顺序早于application.yml,作用是读取nacos中配置文件。
# @xxx@ 从pom.xml中取值, 所以 @xx@ 标注的值,都不能从nacos中获取
pinda:
nacos:
# 配置文件从pd-parent.pom中加载
ip: ${NACOS_IP:@pom.nacos.ip@}
port: ${NACOS_PORT:@pom.nacos.port@}
namespace: ${NACOS_ID:@pom.nacos.namespace@}
spring:
main:
allow-bean-definition-overriding: true
application:
name: @project.artifactId@
profiles: # 当前环境为dev
active: @pom.profile.name@
cloud:
nacos:
config: # 配置中心相关
server-addr: ${pinda.nacos.ip}:${pinda.nacos.port}
file-extension: yml
namespace: ${pinda.nacos.namespace}
shared-dataids: common.yml,redis.yml,mysql.yml
refreshable-dataids: common.yml
enabled: true
discovery: # 服务注册中心相关
server-addr: ${pinda.nacos.ip}:${pinda.nacos.port}
namespace: ${pinda.nacos.namespace}
metadata: # 元数据,用于权限服务实时获取各个服务的所有接口
management.context-path: ${server.servlet.context-path:}${spring.mvc.servlet.path:}${management.endpoints.web.base-path:}
aop:
proxy-target-class: true
auto: true
# 只能配置在bootstrap.yml ,否则会生成 log.path_IS_UNDEFINED 文件夹
# window会自动在 代码所在盘 根目录下自动创建文件夹, 如: D:/data/projects/logs
logging:
file:
path: /data/projects/logs
name: ${logging.file.path}/${spring.application.name}/root.log
# 用于/actuator/info
info:
name: '@project.name@'
description: '@project.description@'
version: '@project.version@'
spring-boot-version: '@spring.boot.version@'
spring-cloud-version: '@spring.cloud.version@'
logback-spring.xml
logback-spring.xml中引用的变量来自于pd-tools-log模块
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<!--引入pd-tools-log的配置文件-->
<include resource="com/itheima/pinda/log/logback/pinda-defaults.xml"/>
<!--level指日志输出级别,appender指日志输出类型比如控制台或者文件-->
<springProfile name="test,docker,prod">
<logger name="com.itheima.pinda.authority.controller" additivity="true"
level="${log.level.controller}">
<appender-ref ref="ASYNC_CONTROLLER_APPENDER"/>
</logger>
<logger name="com.itheima.pinda.authority.biz.service" additivity="true"
level="${log.level.service}">
<appender-ref ref="ASYNC_SERVICE_APPENDER"/>
</logger>
<logger name="com.itheima.pinda.authority.biz.dao" additivity="false"
level="${log.level.dao}">
<appender-ref ref="ASYNC_DAO_APPENDER"/>
</logger>
</springProfile>
<springProfile name="dev">
<logger name="com.itheima.pinda.authority.controller" additivity="true"
level="${log.level.controller}">
<appender-ref ref="CONTROLLER_APPENDER"/>
</logger>
<logger name="com.itheima.pinda.authority.biz.service" additivity="true"
level="${log.level.service}">
<appender-ref ref="SERVICE_APPENDER"/>
</logger>
</springProfile>
</configuration>
j2cache配置文件
在当前pd-auth-server项目中会使用到j2cache来操作缓存,在Nacos配置中心的redis.yml中已经配置了j2cache的相关配置:
redis.yml配置文件存在于nacos中,配置了一二级缓存信息
j2cache:
# config-location: /j2cache.properties
open-spring-cache: true
cache-clean-mode: passive
allow-null-values: true
redis-client: lettuce
l2-cache-open: true
# l2-cache-open: false # 关闭二级缓存
broadcast: net.oschina.j2cache.cache.support.redis.SpringRedisPubSubPolicy
# broadcast: jgroups # 关闭二级缓存
L1:
provider_class: caffeine
L2:
provider_class: net.oschina.j2cache.cache.support.redis.SpringRedisProvider
config_section: lettuce
sync_ttl_to_redis: true
default_cache_null_object: false
serialization: fst
caffeine:
properties: /j2cache/caffeine.properties # 这个配置文件需要放在项目中
lettuce:
mode: single
namespace:
storage: generic
channel: j2cache
scheme: redis
hosts: ${pinda.redis.ip}:${pinda.redis.port}
password: ${pinda.redis.password}
database: ${pinda.redis.database}
sentinelMasterId:
maxTotal: 100
maxIdle: 10
minIdle: 10
timeout: 10000
通过上面的配置可以看到,还需要在项目中提供/j2cache/caffeine.properties,文件内容如下:
#########################################
# Caffeine configuration
# \u6682\u65F6\u6CA1\u7528
# [name] = size, xxxx[s|m|h|d]
#########################################
default=2000, 2h
captcha=1000, 5m
resource=2000, 2h
user_resource=3000, 2h
密钥文件
JWT签名算法中,一般有两个选择:HS256和RS256。
HS256 (带有 SHA-256 的 HMAC )是一种对称加密算法, 双方之间仅共享一个密钥。由于使用相同的密钥生成签名和验证签名, 因此必须注意确保密钥不被泄密。
RS256 (采用SHA-256 的 RSA 签名) 是一种非对称加密算法, 它使用公共/私钥对: JWT的提供方采用私钥生成签名, JWT 的使用方获取公钥以验证签名。
在Nacos配置中心的pd-auth-server.yml中通过配置的形式已经指定了这两个配置文件的位置和名称:
authentication:
user:
header-name: token
expire: 43200 # 外部token有效期为12小时
pri-key: client/pri.key # 加密
pub-key: client/pub.key # 解密
spy.properties
spy.properties是p6spy所需的属性文件。p6spy是一个开源项目,通常使用它来跟踪数据库操作,查看程序运行过程中执行的sql语句,还可以输出执行sql语句消耗的时间。
在Nacos配置中心的pd-auth-server-dev.yml中进行了如下配置:
pd-auth-server-dev.yml此配置文件只针对dev环境p6spy进行sql语句输出,对于prod环境不需要使用p6spy
# p6spy是一个开源项目,通常使用它来跟踪数据库操作,查看程序运行过程中执行的sql语句
# 开发环境需要使用p6spy进行sql语句输出
# 但p6spy会有性能损耗,不适合在生产线使用,故其他环境无需配置
spring:
datasource:
driver-class-name: com.p6spy.engine.spy.P6SpyDriver
url: jdbc:p6spy:mysql://${pinda.mysql.ip}:${pinda.mysql.port}/${pinda.mysql.database}?serverTimezone=CTT&characterEncoding=utf8&useUnicode=true&useSSL=false&autoReconnect=true&zeroDateTimeBehavior=convertToNull&allowMultiQueries=true
db-type: mysql
我们在开发阶段使用的数据源其实就是P6Spy提供的数据源,这样就可以在控制台打印sql已经sql执行的时间了。
spy.properties是p6spy所需的属性文件。
spy.properties配置文件内容如下:
module.log=com.p6spy.engine.logging.P6LogFactory,com.p6spy.engine.outage.P6OutageFactory
logMessageFormat=com.baomidou.mybatisplus.extension.p6spy.P6SpyLogger
appender=com.baomidou.mybatisplus.extension.p6spy.StdoutLogger
deregisterdrivers=true
useprefix=true
excludecategories=info,debug,result,commit,resultset
dateformat=yyyy-MM-dd HH:mm:ss
driverlist=com.mysql.cj.jdbc.Driver
outagedetection=true
outagedetectioninterval=2
dozer
Dozer是Java Bean到Java Bean映射器
在resources下创建dozer目录并提供biz.dozer.xml和global.dozer.xml文件,内容如下:
biz.dozer.xml
<?xml version="1.0" encoding="UTF-8"?>
<mappings xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns="http://dozermapper.github.io/schema/bean-mapping"
xsi:schemaLocation="http://dozermapper.github.io/schema/bean-mapping
http://dozermapper.github.io/schema/bean-mapping.xsd">
<mapping date-format="yyyy-MM-dd HH:mm:ss">
<class-a>com.itheima.pinda.authority.entity.auth.Menu</class-a>
<class-b>com.itheima.pinda.authority.dto.auth.VueRouter</class-b>
<field>
<a>name</a>
<b>meta.title</b>
</field>
<field>
<a>name</a>
<b>name</b>
</field>
<field>
<a>icon</a>
<b>meta.icon</b>
</field>
</mapping>
</mappings>
global.dozer.xml
<?xml version="1.0" encoding="UTF-8"?>
<mappings xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns="http://dozermapper.github.io/schema/bean-mapping"
xsi:schemaLocation="http://dozermapper.github.io/schema/bean-mapping
http://dozermapper.github.io/schema/bean-mapping.xsd">
<!--
@see: http://www.jianshu.com/p/bf8f0e8aee23
@see: http://blog.csdn.net/whhahyy/article/details/48594657
全局配置:
<date-format>表示日期格式
<stop-on-errors>错误处理开关
<wildcard>通配符
<trim-strings>裁剪字符串开关
-->
<configuration>
<date-format>yyyy-MM-dd HH:mm:ss</date-format>
</configuration>
</mappings>
配置类
全局异常处理的配置类:
继承DefaultGlobalExceptionHandler类的一个全局异常处理的配置类
import com.itheima.pinda.common.handler.DefaultGlobalExceptionHandler;
import org.springframework.context.annotation.Configuration;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.ControllerAdvice;
import org.springframework.web.bind.annotation.ResponseBody;
import org.springframework.web.bind.annotation.RestController;
/**
* 全局异常处理
*/
@Configuration
@ControllerAdvice(annotations = {RestController.class, Controller.class})
@ResponseBody
public class ExceptionConfiguration extends DefaultGlobalExceptionHandler {
}
公共基础的配置类:
import com.itheima.pinda.common.config.BaseConfig;
import org.springframework.context.annotation.Configuration;
@Configuration
public class AuthorityWebConfiguration extends BaseConfig {
}
数据库相关的配置类:
import cn.hutool.core.util.ArrayUtil;
import com.alibaba.druid.spring.boot.autoconfigure.DruidDataSourceBuilder;
import com.baomidou.mybatisplus.autoconfigure.ConfigurationCustomizer;
import com.baomidou.mybatisplus.autoconfigure.MybatisPlusProperties;
import com.baomidou.mybatisplus.autoconfigure.MybatisPlusPropertiesCustomizer;
import com.itheima.pinda.database.datasource.BaseDatabaseConfiguration;
import com.itheima.pinda.database.properties.DatabaseProperties;
import com.p6spy.engine.spy.P6DataSource;
import lombok.extern.slf4j.Slf4j;
import org.apache.ibatis.mapping.DatabaseIdProvider;
import org.apache.ibatis.plugin.Interceptor;
import org.apache.ibatis.scripting.LanguageDriver;
import org.apache.ibatis.session.ExecutorType;
import org.apache.ibatis.session.SqlSessionFactory;
import org.apache.ibatis.type.TypeHandler;
import org.mybatis.spring.SqlSessionTemplate;
import org.mybatis.spring.annotation.MapperScan;
import org.springframework.aop.Advisor;
import org.springframework.beans.factory.ObjectProvider;
import org.springframework.beans.factory.annotation.Qualifier;
import org.springframework.boot.context.properties.ConfigurationProperties;
import org.springframework.boot.context.properties.EnableConfigurationProperties;
import org.springframework.context.ApplicationContext;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.core.io.ResourceLoader;
import org.springframework.jdbc.datasource.DataSourceTransactionManager;
import org.springframework.stereotype.Repository;
import org.springframework.transaction.PlatformTransactionManager;
import org.springframework.transaction.interceptor.TransactionInterceptor;
import javax.sql.DataSource;
import java.util.List;
@Configuration
@Slf4j
//mybatis相关mapper扫描,扫描com.itheima.pinda包,annotationClass注解标识
@MapperScan(
basePackages = {"com.itheima.pinda",},
annotationClass = Repository.class,
//sqlSessionFactory
sqlSessionFactoryRef = AuthorityDatabaseAutoConfiguration.DATABASE_PREFIX + "SqlSessionFactory")
//开启配置属性
@EnableConfigurationProperties({MybatisPlusProperties.class, DatabaseProperties.class})
public class AuthorityDatabaseAutoConfiguration extends BaseDatabaseConfiguration {
/**
* 每个数据源配置不同即可
*/
final static String DATABASE_PREFIX = "master";
//构造方法
public AuthorityDatabaseAutoConfiguration(MybatisPlusProperties properties,
DatabaseProperties databaseProperties,
ObjectProvider<Interceptor[]> interceptorsProvider,
ObjectProvider<TypeHandler[]> typeHandlersProvider,
ObjectProvider<LanguageDriver[]> languageDriversProvider,
ResourceLoader resourceLoader,
ObjectProvider<DatabaseIdProvider> databaseIdProvider,
ObjectProvider<List<ConfigurationCustomizer>> configurationCustomizersProvider,
ObjectProvider<List<MybatisPlusPropertiesCustomizer>> mybatisPlusPropertiesCustomizerProvider,
ApplicationContext applicationContext) {
super(properties, databaseProperties, interceptorsProvider, typeHandlersProvider,
languageDriversProvider, resourceLoader, databaseIdProvider,
configurationCustomizersProvider, mybatisPlusPropertiesCustomizerProvider, applicationContext);
}
//模板对象,spring封装的,需要注入SqlSessionFactory
@Bean(DATABASE_PREFIX + "SqlSessionTemplate")
public SqlSessionTemplate getSqlSessionTemplate(@Qualifier(DATABASE_PREFIX + "SqlSessionFactory") SqlSessionFactory sqlSessionFactory) {
ExecutorType executorType = this.properties.getExecutorType();
if (executorType != null) {
return new SqlSessionTemplate(sqlSessionFactory, executorType);
} else {
return new SqlSessionTemplate(sqlSessionFactory);
}
}
/**
* 数据源信息
* 开发环境创建出P6DataSource数据源,别的环境创建出DruidDataSource
*
* @return
*/
@Bean(name = DATABASE_PREFIX + "DruidDataSource")
@ConfigurationProperties(prefix = "spring.datasource.druid")
public DataSource druidDataSource() {
return DruidDataSourceBuilder.create().build();
}
@Bean(name = DATABASE_PREFIX + "DataSource")
public DataSource dataSource(@Qualifier(DATABASE_PREFIX + "DruidDataSource") DataSource dataSource) {
//判断是否是dev环境
if (ArrayUtil.contains(DEV_PROFILES, this.profiles)) {
return new P6DataSource(dataSource);
} else {
return dataSource;
}
}
/**
* mybatis Sql Session 工厂
*
* @return
* @throws Exception
*/
@Bean(DATABASE_PREFIX + "SqlSessionFactory")
public SqlSessionFactory getSqlSessionFactory(@Qualifier(DATABASE_PREFIX + "DataSource") DataSource dataSource) throws Exception {
return super.sqlSessionFactory(dataSource);
}
/**
* 数据源事务管理器
*
* @return
*/
@Bean(name = DATABASE_PREFIX + "TransactionManager")
public DataSourceTransactionManager dsTransactionManager(@Qualifier(DATABASE_PREFIX + "DataSource") DataSource dataSource) {
return new DataSourceTransactionManager(dataSource);
}
/**
* 事务拦截器
*
* @param transactionManager
* @return
*/
@Bean(DATABASE_PREFIX + "TransactionInterceptor")
public TransactionInterceptor transactionInterceptor(@Qualifier(DATABASE_PREFIX + "TransactionManager") PlatformTransactionManager transactionManager) {
return new TransactionInterceptor(transactionManager, this.transactionAttributeSource());
}
/**
* 事务 Advisor
*
* @param transactionManager
* @return
*/
@Bean(DATABASE_PREFIX + "Advisor")
public Advisor getAdvisor(@Qualifier(DATABASE_PREFIX + "TransactionManager") PlatformTransactionManager transactionManager, @Qualifier(DATABASE_PREFIX + "TransactionInterceptor") TransactionInterceptor ti) {
return super.txAdviceAdvisor(ti);
}
}
mybatis框架相关的配置类:
import com.itheima.pinda.database.datasource.BaseMybatisConfiguration;
import com.itheima.pinda.database.properties.DatabaseProperties;
import lombok.extern.slf4j.Slf4j;
import org.springframework.context.annotation.Configuration;
/**
* Mybatis相关配置
*/
@Configuration
@Slf4j
public class AuthorityMybatisAutoConfiguration extends BaseMybatisConfiguration {
public AuthorityMybatisAutoConfiguration(DatabaseProperties databaseProperties) {
super(databaseProperties);
}
}
启动类
import com.itheima.pinda.auth.server.EnableAuthServer;
import com.itheima.pinda.user.annotation.EnableLoginArgResolver;
import com.itheima.pinda.validator.config.EnableFormValidator;
import lombok.extern.slf4j.Slf4j;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
import org.springframework.cloud.client.discovery.EnableDiscoveryClient;
import org.springframework.cloud.openfeign.EnableFeignClients;
import org.springframework.context.ConfigurableApplicationContext;
import org.springframework.context.annotation.EnableAspectJAutoProxy;
import org.springframework.core.env.Environment;
import java.net.InetAddress;
import java.net.UnknownHostException;
@SpringBootApplication
@EnableDiscoveryClient //开启nacos服务发现功能
@EnableAuthServer //jwt utils工具类,生成解析jwt
@EnableFeignClients(value = { //开启Feign客户端进行接口调用
"com.itheima.pinda",
})
@Slf4j //日志
@EnableAspectJAutoProxy(proxyTargetClass = true, exposeProxy = true) //自动代理,AOP
@EnableLoginArgResolver //参数解析器,当前登录user自动注入
@EnableFormValidator //hibernate-validator表单校验
public class AuthorityApplication {
public static void main(String[] args) throws UnknownHostException {
//ApplicationContext对象
ConfigurableApplicationContext application =
SpringApplication.run(AuthorityApplication.class, args);
Environment env = application.getEnvironment();
//日志输出
log.info("应用 '{}' 运行成功! Swagger文档: http://{}:{}/doc.html",
//获取配置文件中某个配置,在本地配置文件中有配置
env.getProperty("spring.application.name"),
//获取ip地址
InetAddress.getLocalHost().getHostAddress(),
//获取端口号,在nacos上配置了
env.getProperty("server.port"));
}
}
开发验证码接口
1,创建LoginController并提供生成验证码的方法
package com.itheima.pinda.authority.controller.auth;
import com.itheima.pinda.authority.biz.service.auth.ValidateCodeService;
import com.itheima.pinda.base.BaseController;
import com.itheima.pinda.base.R;
import io.swagger.annotations.Api;
import io.swagger.annotations.ApiOperation;
import lombok.extern.slf4j.Slf4j;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.web.bind.annotation.*;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
/**
* 登录
*/
@RestController
@RequestMapping("/anno")
@Api(value = "UserAuthController", tags = "登录")//swagger文档接口
@Slf4j
public class LoginController extends BaseController {
@Autowired
private ValidateCodeService validateCodeService;
@ApiOperation(value = "验证码", notes = "验证码")
@GetMapping(value = "/captcha", produces = "image/png")
public void captcha(@RequestParam(value = "key") String key,
HttpServletResponse response) throws IOException {
this.validateCodeService.create(key, response);
}
}
2,创建ValidateCodeService接口
import java.io.IOException;
import javax.servlet.http.HttpServletResponse;
/**
* 验证码
*/
public interface ValidateCodeService {
/**
* 生成验证码
*/
void create(String key, HttpServletResponse response) throws IOException;
}
3,创建ValidateCodeServiceImpl
import java.io.IOException;
import javax.servlet.http.HttpServletResponse;
import com.itheima.pinda.authority.biz.service.auth.ValidateCodeService;
import com.itheima.pinda.common.constant.CacheKey;
import com.itheima.pinda.exception.BizException;
import com.wf.captcha.ArithmeticCaptcha;
import net.oschina.j2cache.CacheChannel;
import net.oschina.j2cache.CacheObject;
import org.apache.commons.lang3.StringUtils;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.http.HttpHeaders;
import org.springframework.http.MediaType;
import org.springframework.stereotype.Service;
/**
* 验证码服务
*/
@Service
public class ValidateCodeServiceImpl implements ValidateCodeService {
@Autowired
private CacheChannel cache;
@Override
public void create(String key,
HttpServletResponse response) throws IOException {
if (StringUtils.isBlank(key)) {
throw BizException.validFail("验证码key不能为空");
}
response.setContentType(MediaType.IMAGE_PNG_VALUE);
response.setHeader(HttpHeaders.PRAGMA, "No-cache");
response.setHeader(HttpHeaders.CACHE_CONTROL, "No-cache");
response.setDateHeader(HttpHeaders.EXPIRES, 0L);
Captcha captcha = new ArithmeticCaptcha(115, 42);
captcha.setCharType(2);
cache.set(CacheKey.CAPTCHA, key, StringUtils.lowerCase(captcha.text()));
captcha.out(response.getOutputStream());
}
}
验证码接口开发完成后可以启动服务,通过接口文档进行测试:
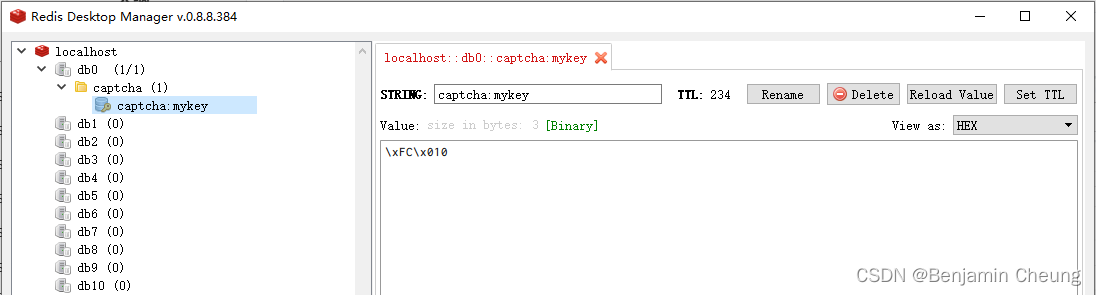
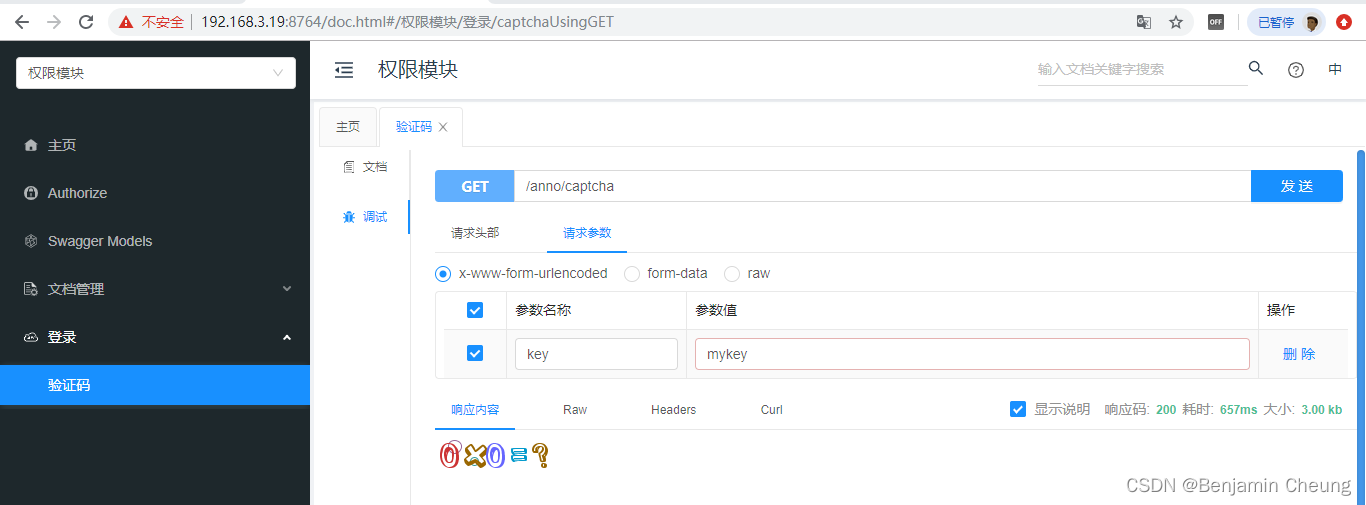 可以看到已经将验证码缓存到redis:
可以看到已经将验证码缓存到redis:
开发认证接口
1,在LoginController中创建login方法
@Autowired
private AuthManager authManager;//认证管理器对象
/**
* 登录认证
*/
@ApiOperation(value = "登录", notes = "登录")
@PostMapping(value = "/login")
public R<LoginDTO> login(@Validated @RequestBody LoginParamDTO login)
throws BizException {
log.info("account={}", login.getAccount());
if (this.validateCodeService.check(login.getKey(), login.getCode())) {
return this.authManager.login(login.getAccount(), login.getPassword());
}
return this.success(null);
}
2,在ValidateCodeService接口中扩展check方法完成校验验证码
/**
* 校验验证码
* @param key 前端上送 key
* @param value 前端上送待校验值
*/
boolean check(String key, String value);
3,在ValidateCodeServiceImpl实现类中实现check方法
//校验验证码
@Override
public boolean check(String key, String value) {
if (StringUtils.isBlank(value)) {
throw BizException.validFail("请输入验证码");
}
//根据key从缓存中获取验证码
CacheObject cacheObject = cache.get(CacheKey.CAPTCHA, key);
if (cacheObject.getValue() == null) {
throw BizException.validFail("验证码已过期");
}
//比对验证码
if (!StringUtils.equalsIgnoreCase(value,
String.valueOf(cacheObject.getValue()))) {
throw BizException.validFail("验证码不正确");
}
//验证通过,立即从缓存中删除验证码
cache.evict(CacheKey.CAPTCHA, key);
return true;
}
4,创建AuthManager认证管理器类,提供用户名密码认证功能
import com.baomidou.mybatisplus.core.toolkit.Wrappers;
import com.itheima.pinda.auth.server.utils.JwtTokenServerUtils;
import com.itheima.pinda.auth.utils.JwtUserInfo;
import com.itheima.pinda.auth.utils.Token;
import com.itheima.pinda.authority.biz.service.auth.ResourceService;
import com.itheima.pinda.authority.dto.auth.LoginDTO;
import com.itheima.pinda.authority.dto.auth.ResourceQueryDTO;
import com.itheima.pinda.authority.dto.auth.UserDTO;
import com.itheima.pinda.authority.entity.auth.Resource;
import com.itheima.pinda.authority.entity.auth.User;
import com.itheima.pinda.base.R;
import com.itheima.pinda.dozer.DozerUtils;
import com.itheima.pinda.exception.BizException;
import com.itheima.pinda.exception.code.ExceptionCode;
import com.itheima.pinda.utils.BizAssert;
import com.itheima.pinda.utils.NumberHelper;
import com.itheima.pinda.authority.biz.service.auth.UserService;
import com.itheima.pinda.utils.TimeUtils;
import lombok.extern.slf4j.Slf4j;
import org.apache.commons.codec.digest.DigestUtils;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Service;
import java.time.LocalDateTime;
import java.util.List;
import java.util.stream.Collectors;
/**
*认证管理器
*/
@Service
@Slf4j
public class AuthManager {
@Autowired
private JwtTokenServerUtils jwtTokenServerUtils;
@Autowired
private UserService userService;
@Autowired
private ResourceService resourceService;
@Autowired
private DozerUtils dozer; //类型转换
/**
* 账号登录
* @param account
* @param password
*/
public R<LoginDTO> login(String account, String password) {
// 登录验证
R<User> result = checkUser(account, password);
if (result.getIsError()) {
return R.fail(result.getCode(), result.getMsg());
}
User user = result.getData();
// 生成jwt token
Token token = this.generateUserToken(user);
List<Resource> resourceList =this.resourceService.
findVisibleResource(ResourceQueryDTO.builder().
userId(user.getId()).build());
List<String> permissionsList = null;
if(resourceList != null && resourceList.size() > 0){
//将用户对应的权限(给前端使用的)
//Resource中code
permissionsList = resourceList.stream().
map(Resource::getCode).
collect(Collectors.toList());
//将用户对应的权限(给后端网关使用的)进行缓存
//Resource中method+url
List<String> visibleResource = resourceList.stream().map(
(resource -> {
return resource.getMethod()+resource.getUrl();
})
).collect(Collectors.toList());
cacheChannel.set(CacheKey.USER_RESOURCE,user.getId().toString(),visibleResource);
}
//封装数据
LoginDTO loginDTO = LoginDTO.builder()
.user(this.dozer.map(user, UserDTO.class))
.token(token)
.permissionsList(permissionsList)
.build();
return R.success(loginDTO);
}
//生成jwt token
private Token generateUserToken(User user) {
JwtUserInfo userInfo = new JwtUserInfo(user.getId(),
user.getAccount(),
user.getName(),
user.getOrgId(),
user.getStationId());
Token token = this.jwtTokenServerUtils.generateUserToken(userInfo, null);
log.info("token={}", token.getToken());
return token;
}
// 登录验证
private R<User> checkUser(String account, String password) {
User user = this.userService.getOne(Wrappers.<User>lambdaQuery()
.eq(User::getAccount, account));
// 密码加密
String passwordMd5 = DigestUtils.md5Hex(password);
if (user == null || !user.getPassword().equals(passwordMd5)) {
return R.fail(ExceptionCode.JWT_USER_INVALID);
}
return R.success(user);
}
}
5,创建UserService接口、UserServiceImpl实现类、UserMapper接口
import com.baomidou.mybatisplus.extension.service.IService;
/**
* 业务接口,继承IService指定实体类
*/
public interface UserService extends IService<User> {
}
import com.baomidou.mybatisplus.extension.service.impl.ServiceImpl;
import com.itheima.pinda.authority.biz.dao.auth.UserMapper;
import com.itheima.pinda.authority.biz.service.auth.UserService;
import com.itheima.pinda.authority.entity.auth.User;
import lombok.extern.slf4j.Slf4j;
import org.springframework.stereotype.Service;
/**
* 业务实现类
*/
@Slf4j
@Service
public class UserServiceImpl extends ServiceImpl<UserMapper, User>
implements UserService {
}
import com.baomidou.mybatisplus.core.mapper.BaseMapper;
import com.itheima.pinda.authority.entity.auth.User;
import org.springframework.stereotype.Repository;
/**
* Mapper 接口
*/
@Repository
public interface UserMapper extends BaseMapper<User> {
}
6,创建ResourceService接口、ResourceServiceImpl实现类、ResourceMapper接口、ResourceMapper.xml
import java.util.List;
import com.baomidou.mybatisplus.extension.service.IService;
import com.itheima.pinda.authority.dto.auth.ResourceQueryDTO;
import com.itheima.pinda.authority.entity.auth.Resource;
/**
* 业务接口
*/
public interface ResourceService extends IService<Resource> {
/**
* 查询 用户拥有的资源权限
*/
List<Resource> findVisibleResource(ResourceQueryDTO resource);
}
import java.util.List;
import java.util.stream.Collectors;
import com.baomidou.mybatisplus.extension.service.impl.ServiceImpl;
import com.itheima.pinda.authority.biz.service.auth.ResourceService;
import com.itheima.pinda.authority.dto.auth.ResourceQueryDTO;
import com.itheima.pinda.authority.entity.auth.Resource;
import com.itheima.pinda.common.constant.CacheKey;
import com.itheima.pinda.exception.BizException;
import com.itheima.pinda.utils.StrHelper;
import com.itheima.pinda.authority.biz.dao.auth.ResourceMapper;
import lombok.extern.slf4j.Slf4j;
import net.oschina.j2cache.CacheChannel;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Service;
/**
* 业务实现类
* 资源
*/
@Slf4j
@Service
public class ResourceServiceImpl extends ServiceImpl<ResourceMapper, Resource> implements ResourceService {
@Autowired
private CacheChannel cache;
/**
* 查询用户的可用资源权限
*/
@Override
public List<Resource> findVisibleResource(ResourceQueryDTO resourceQueryDTO) {
//查询当前用户可访问的资源
List<Resource> visibleResource =
baseMapper.findVisibleResource(resourceQueryDTO);
if(visibleResource != null && visibleResource.size() > 0){
List<String> userResource = visibleResource.
stream().
map((Resource r) -> {
return r.getMethod() + r.getUrl();
}).collect(Collectors.toList());
//将当前用户可访问的资源载入缓存,形式为:GET/user/page
cache.set(CacheKey.USER_RESOURCE,
resourceQueryDTO.getUserId().toString(),
userResource);
}
return visibleResource;
}
}
import java.util.List;
import com.baomidou.mybatisplus.core.mapper.BaseMapper;
import com.itheima.pinda.authority.dto.auth.ResourceQueryDTO;
import com.itheima.pinda.authority.entity.auth.Resource;
import org.springframework.stereotype.Repository;
/**
* Mapper 接口
*/
@Repository
public interface ResourceMapper extends BaseMapper<Resource> {
/**
* 查询用户拥有的资源权限
*/
List<Resource> findVisibleResource(ResourceQueryDTO resource);
}
在resources目录下创建mapper_authority目录,在此目录中创建ResourceMapper.xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE mapper PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN" "http://mybatis.org/dtd/mybatis-3-mapper.dtd">
<mapper namespace="com.itheima.pinda.authority.biz.dao.auth.ResourceMapper">
<!-- 通用查询映射结果 -->
<resultMap id="BaseResultMap"
type="com.itheima.pinda.authority.entity.auth.Resource">
<id column="id" jdbcType="BIGINT" property="id"/>
<result column="create_user" jdbcType="BIGINT" property="createUser"/>
<result column="create_time" jdbcType="TIMESTAMP" property="createTime"/>
<result column="update_user" jdbcType="BIGINT" property="updateUser"/>
<result column="update_time" jdbcType="TIMESTAMP" property="updateTime"/>
<result column="code" jdbcType="VARCHAR" property="code"/>
<result column="name" jdbcType="VARCHAR" property="name"/>
<result column="menu_id" jdbcType="BIGINT" property="menuId"/>
<result column="describe_" jdbcType="VARCHAR" property="describe"/>
<result column="method" jdbcType="VARCHAR" property="method"/>
<result column="url" jdbcType="VARCHAR" property="url"/>
</resultMap>
<!-- 通用查询结果列 -->
<sql id="Base_Column_List">
id, create_user, create_time, update_user, update_time,
code, name, menu_id, describe_,method,url
</sql>
<select id="findVisibleResource" resultMap="BaseResultMap">
SELECT
<include refid="Base_Column_List"/>
from pd_auth_resource where 1=1
and id in (
SELECT authority_id FROM pd_auth_role_authority ra INNER JOIN pd_auth_user_role ur on ra.role_id = ur.role_id
INNER JOIN pd_auth_role r on r.id = ra.role_id
where ur.user_id = #{userId, jdbcType=BIGINT} and r.`status` = true
and ra.authority_type = 'RESOURCE'
)
</select>
</mapper>
7,认证接口开发完成后可以使用接口文档进行测试:
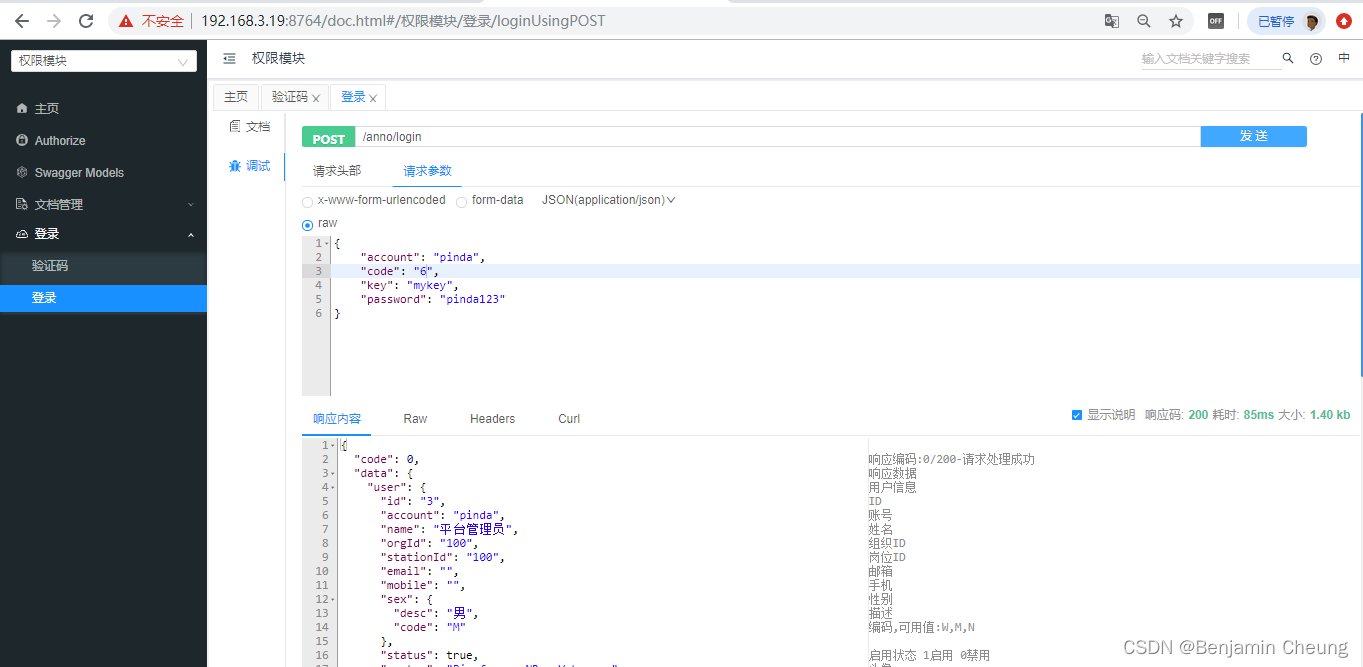
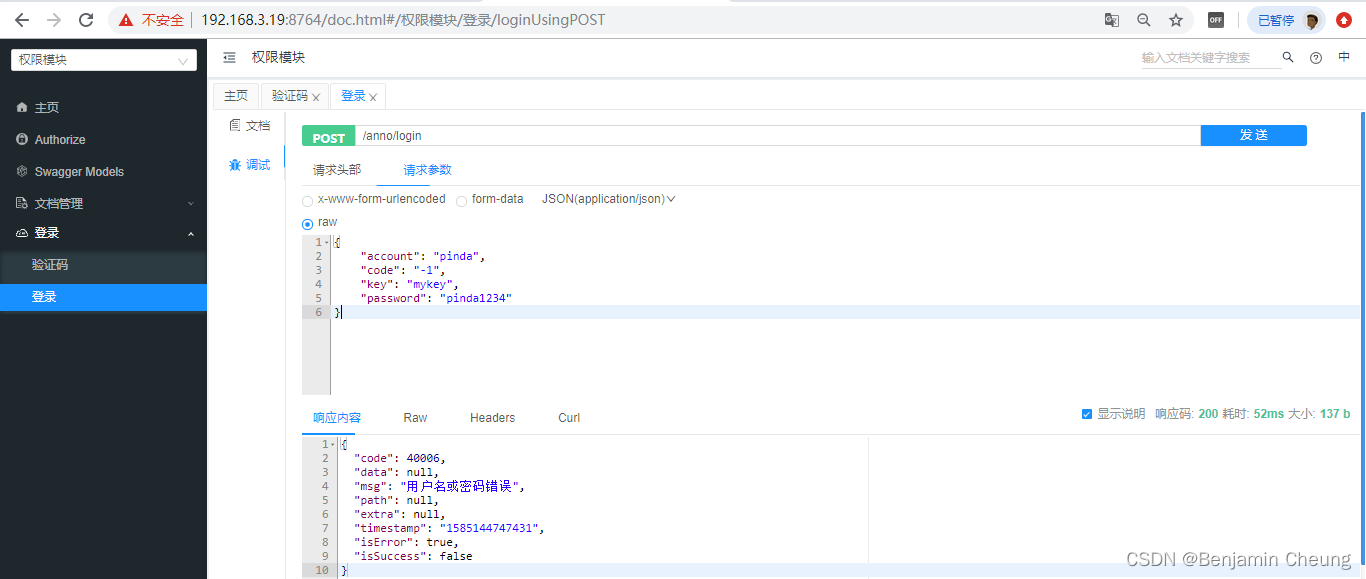
开发操作日志功能
当前的权限服务已经依赖了pd-tools-log日志模块,此模块中已经定义好了SysLogAspect切面类用于拦截Controller中添加@SysLog注解的方法,在切面类中通过前置通知和后置通知方法收集操作日志相关信息并发布SysLogEvent日志事件,通过定义SysLogListener监听器来监听日志事件。
在权限服务中只需要定义配置类来创建SysLogListener,同时将SysLogListener所需的Consumer参数传递进行即可。
具体开发步骤:
1,创建OptLogService接口
import com.baomidou.mybatisplus.extension.service.IService;
import com.itheima.pinda.authority.entity.common.OptLog;
import com.itheima.pinda.log.entity.OptLogDTO;
/**
* 业务接口
* 操作日志
*/
public interface OptLogService extends IService<OptLog> {
/**
* 保存日志
*/
boolean save(OptLogDTO entity);
}
2,创建OptLogServiceImpl实现类
import com.baomidou.mybatisplus.extension.service.impl.ServiceImpl;
import com.itheima.pinda.authority.biz.dao.common.OptLogMapper;
import com.itheima.pinda.authority.entity.common.OptLog;
import com.itheima.pinda.dozer.DozerUtils;
import com.itheima.pinda.log.entity.OptLogDTO;
import com.itheima.pinda.authority.biz.service.common.OptLogService;
import lombok.extern.slf4j.Slf4j;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Service;
/**
* 业务实现类
* 操作日志
*/
@Slf4j
@Service
public class OptLogServiceImpl extends ServiceImpl<OptLogMapper, OptLog>
implements OptLogService {
@Autowired
DozerUtils dozer;//类型转换
@Override
public boolean save(OptLogDTO entity) {
return super.save(dozer.map(entity, OptLog.class));
}
}
3,创建OptLogMapper接口
import com.baomidou.mybatisplus.core.mapper.BaseMapper;
import com.itheima.pinda.authority.entity.common.OptLog;
import org.springframework.stereotype.Repository;
/**
* Mapper 接口
* 系统日志
*/
@Repository
public interface OptLogMapper extends BaseMapper<OptLog> {
}
4,创建SysLogConfiguration配置类
import com.itheima.pinda.authority.biz.service.common.OptLogService;
import com.itheima.pinda.log.entity.OptLogDTO;
import com.itheima.pinda.log.event.SysLogListener;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.scheduling.annotation.EnableAsync;
import java.util.function.Consumer;
/**
* 日志自动配置
*/
@EnableAsync
@Configuration
public class SysLogConfiguration {
//日志记录监听器
@Bean
public SysLogListener sysLogListener(OptLogService optLogService) {
Consumer<OptLogDTO> consumer = (optLog) -> optLogService.save(optLog);
return new SysLogListener(consumer);
}
}
5,在已经开发的Controller的方法上加入@SysLog注解,然后通过接口文档访问,可以看到操作日志已经插入到pd_common_opt_log日志表中了。
网关服务开发
pd-gateway作为通用权限系统的网关服务,前端的http请求首先需要经过网关服务处理,再通过网关服务的路由功能转发到权限服务或者其他微服务进行业务处理。我们可以在网关服务进行统一的jwt令牌解析、鉴权相关操作。
配置文件
bootstrap.yml
由于我们当前使用的是Nacos作为整个项目的配置中心,所以Spring Boot的大部分配置文件都在Nacos中进行统一配置,我们的项目中只需要按照Spring Boot的要求在resources目录下提供bootstrap.yml配置文件即可,文件内容如下:
pinda:
# docker部署时,需要指定, 表示运行该服务的宿主机IP
local-ip: ${LOCAL_IP:${spring.cloud.client.ip-address}}
nacos:
ip: ${NACOS_IP:@pom.nacos.ip@}
port: ${NACOS_PORT:@pom.nacos.port@}
namespace: ${NACOS_ID:@pom.nacos.namespace@}
spring:
main:
allow-bean-definition-overriding: true
application:
name: @project.artifactId@ #pd-gateway
profiles:
active: @pom.profile.name@ #dev
cloud:
nacos:
config:
server-addr: ${pinda.nacos.ip}:${pinda.nacos.port}
file-extension: yml
namespace: ${pinda.nacos.namespace}
shared-dataids: common.yml,redis.yml,mysql.yml
refreshable-dataids: common.yml
enabled: true
discovery:
server-addr: ${pinda.nacos.ip}:${pinda.nacos.port}
namespace: ${pinda.nacos.namespace}
metadata:
management.context-path: ${server.servlet.context-path:}${spring.mvc.servlet.path:}${management.endpoints.web.base-path:}
#http://localhost:8760/api/gate/actuator
logback-spring.xml
由于pd-gateway已经添加了pd-tools-log模块的依赖,所以可以在项目中使用logback记录日志信息。在resources目录下提供logback-spring.xml配置文件,Spring Boot默认就可以加载到,文件内容如下:
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<include resource="com/itheima/pinda/log/logback/pinda-defaults.xml"/>
<springProfile name="test,docker,prod">
<logger name="com.itheima.pinda.zuul" additivity="true" level="INFO">
<appender-ref ref="ASYNC_CONTROLLER_APPENDER"/>
</logger>
</springProfile>
<springProfile name="dev">
<logger name="com.itheima.pinda.zuul" additivity="true" level="INFO">
<appender-ref ref="CONTROLLER_APPENDER"/>
</logger>
</springProfile>
</configuration>
j2cache配置文件
在当前pd-gateway项目中会使用到j2cache来操作缓存,在Nacos配置中心的redis.yml中已经配置了j2cache的相关配置:
j2cache:
# config-location: /j2cache.properties
open-spring-cache: true
cache-clean-mode: passive
allow-null-values: true
redis-client: lettuce
l2-cache-open: true
# l2-cache-open: false # 关闭二级缓存
broadcast: net.oschina.j2cache.cache.support.redis.SpringRedisPubSubPolicy
# broadcast: jgroups # 关闭二级缓存
L1:
provider_class: caffeine
L2:
provider_class: net.oschina.j2cache.cache.support.redis.SpringRedisProvider
config_section: lettuce
sync_ttl_to_redis: true
default_cache_null_object: false
serialization: fst
caffeine:
properties: /j2cache/caffeine.properties # 这个配置文件需要放在项目中
lettuce:
mode: single
namespace:
storage: generic
channel: j2cache
scheme: redis
hosts: ${pinda.redis.ip}:${pinda.redis.port}
password: ${pinda.redis.password}
database: ${pinda.redis.database}
sentinelMasterId:
maxTotal: 100
maxIdle: 10
minIdle: 10
timeout: 10000
通过上面的配置可以看到,还需要在项目中提供/j2cache/caffeine.properties,文件内容如下:
#########################################
# Caffeine configuration
# \u6682\u65F6\u6CA1\u7528
# [name] = size, xxxx[s|m|h|d]
#########################################
default=2000, 2h
resource=2000, 1h
密钥文件
JWT签名算法中,一般有两个选择:HS256和RS256。
HS256 (带有 SHA-256 的 HMAC )是一种对称加密算法, 双方之间仅共享一个密钥。由于使用相同的密钥生成签名和验证签名, 因此必须注意确保密钥不被泄密。
RS256 (采用SHA-256 的 RSA 签名) 是一种非对称加密算法, 它使用公共/私钥对: JWT的提供方采用私钥生成签名, JWT 的使用方获取公钥以验证签名。
本项目中使用RS256非对称加密算法进行签名,这就需要使用RSA生成一对公钥和私钥。在授课资料中已经提供了一对公钥和私钥,其中pub.key为公钥,pri.key为私钥。
前面我们已经提到,在当前网关服务中我们需要对客户端请求中携带的jwt token进行解析,只需要公钥就可以。将授课资料中的pub.key文件复制到pd-gateway项目的resources/client下。
启动类
import com.itheima.pinda.auth.client.EnableAuthClient;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
import org.springframework.cloud.client.discovery.EnableDiscoveryClient;
import org.springframework.cloud.netflix.zuul.EnableZuulProxy;
import org.springframework.cloud.openfeign.EnableFeignClients;
@SpringBootApplication
@EnableDiscoveryClient //nacos服务发现
@EnableFeignClients({"com.itheima.pinda"})
@EnableZuulProxy//开启网关代理
@EnableAuthClient//开启授权客户端,开启后就可以使用pd-tools-jwt提供的工具类进行jwt token解析了
public class ZuulServerApplication {
public static void main(String[] args) {
SpringApplication.run(ZuulServerApplication.class,args);
}
}
配置类
import com.itheima.pinda.common.config.BaseConfig;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.web.cors.UrlBasedCorsConfigurationSource;
import org.springframework.web.filter.CorsFilter;
/**
* 解决跨域问题
*/
@Configuration
public class ZuulConfiguration extends BaseConfig {
@Bean
public CorsFilter corsFilter() {
final UrlBasedCorsConfigurationSource source =
new UrlBasedCorsConfigurationSource();
final org.springframework.web.cors.CorsConfiguration config =
new org.springframework.web.cors.CorsConfiguration();
// 允许cookies跨域
config.setAllowCredentials(true);
// #允许向该服务器提交请求的URI,*表示全部允许
config.addAllowedOrigin("*");
// #允许访问的头信息,*表示全部
config.addAllowedHeader("*");
// 预检请求的缓存时间(秒),即在这个时间段里,对于相同的跨域请求不会再预检了
config.setMaxAge(18000L);
// 允许提交请求的方法,*表示全部允许
config.addAllowedMethod("OPTIONS");
config.addAllowedMethod("HEAD");
// 允许Get的请求类型
config.addAllowedMethod("GET");
config.addAllowedMethod("PUT");
config.addAllowedMethod("POST");
config.addAllowedMethod("DELETE");
config.addAllowedMethod("PATCH");
source.registerCorsConfiguration("/**", config);
return new CorsFilter(source);
}
}
API接口和熔断器
在网关服务中会通过Feign来调用权限服务获取相关信息,所以需要定义API接口和对应的熔断器类
import com.itheima.pinda.authority.dto.auth.ResourceQueryDTO;
import com.itheima.pinda.authority.entity.auth.Resource;
import com.itheima.pinda.base.R;
import org.springframework.cloud.openfeign.FeignClient;
import org.springframework.web.bind.annotation.GetMapping;
import java.util.List;
@FeignClient(name = "${pinda.feign.authority-server:pd-auth-server}",
//熔断器
fallback = ResourceApiFallback.class)
public interface ResourceApi {
//获取所有需要鉴权的资源
@GetMapping("/resource/list")
public R<List> list();
//查询当前登录用户拥有的资源权限
@GetMapping("/resource")
public R<List<Resource>> visible(ResourceQueryDTO resource);
}
import com.itheima.pinda.authority.dto.auth.ResourceQueryDTO;
import com.itheima.pinda.authority.entity.auth.Resource;
import com.itheima.pinda.base.R;
import org.springframework.stereotype.Component;
import java.util.List;
/**
* 资源API熔断
*/
@Component
public class ResourceApiFallback implements ResourceApi {
public R<List> list() {
return null;
}
public R<List<Resource>> visible(ResourceQueryDTO resource) {
return null;
}
}
过滤器
在网关服务中我们需要通过过滤器来实现jwt token解析和鉴权相关处理。
BaseFilter
BaseFilter作为基础过滤器,统一抽取一些公共属性和方法。
import javax.servlet.http.HttpServletRequest;
import com.itheima.pinda.base.R;
import com.itheima.pinda.common.adapter.IgnoreTokenConfig;
import com.netflix.zuul.ZuulFilter;
import com.netflix.zuul.context.RequestContext;
import lombok.extern.slf4j.Slf4j;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.beans.factory.annotation.Value;
import org.springframework.cloud.netflix.zuul.filters.RouteLocator;
/**
* 基础 网关过滤器
*/
@Slf4j
public abstract class BaseFilter extends ZuulFilter {
@Value("${server.servlet.context-path}")
protected String zuulPrefix;
/**
* 判断当前请求uri是否需要忽略
*/
protected boolean isIgnoreToken() {
HttpServletRequest request =
RequestContext.getCurrentContext().getRequest();
String uri = request.getRequestURI();
uri = StrUtil.subSuf(uri, zuulPrefix.length());
uri = StrUtil.subSuf(uri, uri.indexOf("/", 1));
boolean ignoreToken = IgnoreTokenConfig.isIgnoreToken(uri);
return ignoreToken;
}
/**
* 网关抛异常
* @param errMsg
* @param errCode
* @param httpStatusCode
*/
protected void errorResponse(String errMsg, int errCode, int httpStatusCode) {
R tokenError = R.fail(errCode, errMsg);
RequestContext ctx = RequestContext.getCurrentContext();
// 返回错误码
ctx.setResponseStatusCode(httpStatusCode);
ctx.addZuulResponseHeader(
"Content-Type", "application/json;charset=UTF-8");
if (ctx.getResponseBody() == null) {
// 返回错误内容
ctx.setResponseBody(tokenError.toString());
// 过滤该请求,不对其进行路由
ctx.setSendZuulResponse(false);
}
}
}
TokenContextFilter
TokenContextFilter过滤器主要作用就是解析请求头中的jwt token并将解析出的用户信息放入zuul的header中供后面的程序使用。
import javax.servlet.http.HttpServletRequest;
import com.itheima.pinda.auth.client.properties.AuthClientProperties;
import com.itheima.pinda.auth.client.utils.JwtTokenClientUtils;
import com.itheima.pinda.auth.utils.JwtUserInfo;
import com.itheima.pinda.base.R;
import com.itheima.pinda.context.BaseContextConstants;
import com.itheima.pinda.exception.BizException;
import com.itheima.pinda.utils.StrHelper;
import com.netflix.zuul.context.RequestContext;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.cloud.netflix.zuul.filters.support.FilterConstants;
import org.springframework.stereotype.Component;
import org.springframework.util.StringUtils;
import static org.springframework.cloud.netflix.zuul.filters.support.FilterConstants.PRE_TYPE;
/**
* 解析token中的用户信息,并将解析出的用户信息放入zuul的header中
*/
@Component
public class TokenContextFilter extends BaseFilter {
@Autowired
private AuthClientProperties authClientProperties;
@Autowired
private JwtTokenClientUtils jwtTokenClientUtils;
@Override
public String filterType() {
// 前置过滤器
return PRE_TYPE;
}
/**
* filterOrder:通过int值来定义过滤器的执行顺序,数字越大,优先级越低
*/
@Override
public int filterOrder() {
/*
一定要在
org.springframework.cloud.netflix.zuul.filters.pre.PreDecorationFilter
过滤器之后执行,因为这个过滤器做了路由,而我们需要这个路由信息来鉴权
这个过滤器会将我们鉴权需要的信息放置在请求上下文中
*/
return FilterConstants.PRE_DECORATION_FILTER_ORDER + 1;
}
/**
* 返回一个boolean类型来判断该过滤器是否要执行
*/
@Override
public boolean shouldFilter() {
return true;
}
//过滤逻辑
@Override
public Object run() {
// 不进行拦截的地址
if (isIgnoreToken()) {
return null;
}
//上下文对象
RequestContext ctx = RequestContext.getCurrentContext();
HttpServletRequest request = ctx.getRequest();
//获取token, 解析,然后将信息放入 header
//1, 获取token
//从配置属性类中获取配置文件路径
//authClientProperties.getUser().getHeaderName() = token
String userToken =
request.getHeader(authClientProperties.getUser().getHeaderName());
//2, 解析token
JwtUserInfo userInfo = null;
try {
userInfo = jwtTokenClientUtils.getUserInfo(userToken);
} catch (BizException e) { //BizException业务异常
//父类的errorResponse方法
errorResponse(e.getMessage(), e.getCode(), 200);
return null;
} catch (Exception e) {
errorResponse("解析token出错", R.FAIL_CODE, 200);
return null;
}
//3, 将信息放入header
if (userInfo != null) {
addHeader(ctx, BaseContextConstants.JWT_KEY_ACCOUNT,
userInfo.getAccount());
addHeader(ctx, BaseContextConstants.JWT_KEY_USER_ID,
userInfo.getUserId());
addHeader(ctx, BaseContextConstants.JWT_KEY_NAME,
userInfo.getName());
addHeader(ctx, BaseContextConstants.JWT_KEY_ORG_ID,
userInfo.getOrgId());
addHeader(ctx, BaseContextConstants.JWT_KEY_STATION_ID,
userInfo.getStationId());
}
return null;
}
//将指定信息放入zuul的header中
private void addHeader(RequestContext ctx, String name, Object value) {
if (StringUtils.isEmpty(value)) {
return;
}
ctx.addZuulRequestHeader(name, StrHelper.encode(value.toString()));
}
}
AccessFilter
AccessFilter过滤器主要进行的是鉴权相关处理。具体的处理逻辑如下:
第1步:判断当前请求uri是否需要忽略
第2步:获取当前请求的请求方式和uri,拼接成GET/user/page这种形式,称为权限标识符
第3步:从缓存中获取所有需要进行鉴权的资源(同样是由资源表的method字段值+url字段值拼接成),如果没有获取到则通过Feign调用权限服务获取并放入缓存中
第4步:判断这些资源是否包含当前请求的权限标识符,如果不包含当前请求的权限标识符,则返回未经授权错误提示
第5步:如果包含当前的权限标识符,则从zuul header中取出用户id,根据用户id取出缓存中的用户拥有的权限,如果没有取到则通过Feign调用权限服务获取并放入缓存,判断用户拥有的权限是否包含当前请求的权限标识符
第6步:如果用户拥有的权限包含当前请求的权限标识符则说明当前用户拥有权限,直接放行
第7步:如果用户拥有的权限不包含当前请求的权限标识符则说明当前用户没有权限,返回未经授权错误提示
import cn.hutool.core.util.StrUtil;
import com.itheima.pinda.authority.dto.auth.ResourceQueryDTO;
import com.itheima.pinda.authority.entity.auth.Resource;
import com.itheima.pinda.base.R;
import com.itheima.pinda.common.constant.CacheKey;
import com.itheima.pinda.context.BaseContextConstants;
import com.itheima.pinda.exception.code.ExceptionCode;
import com.itheima.pinda.zuul.api.ResourceApi;
import com.netflix.zuul.context.RequestContext;
import lombok.extern.slf4j.Slf4j;
import net.oschina.j2cache.CacheChannel;
import net.oschina.j2cache.CacheObject;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.cloud.netflix.zuul.filters.support.FilterConstants;
import org.springframework.stereotype.Component;
import java.util.List;
import java.util.stream.Collectors;
import static org.springframework.cloud.netflix.zuul.filters.support.FilterConstants.PRE_TYPE;
/**
* 权限验证过滤器
*/
@Component
@Slf4j
public class AccessFilter extends BaseFilter {
@Autowired
private CacheChannel cacheChannel;
@Autowired
private ResourceApi resourceApi;
@Override
public String filterType() {
return PRE_TYPE;
}
@Override
public int filterOrder() {
return FilterConstants.PRE_DECORATION_FILTER_ORDER + 10;
}
@Override
public boolean shouldFilter() {
return true;
}
/**
* 验证当前用户是否拥有某个URI的访问权限
*/
@Override
public Object run() {
//第1步:判断当前请求uri是否需要忽略
// 不进行拦截的地址
if (isIgnoreToken()) {
return null;
}
//第2步:获取当前请求的请求方式和uri,拼接成GET/user/page这种形式,称为权限标识符
RequestContext requestContext = RequestContext.getCurrentContext();
String requestURI = requestContext.getRequest().getRequestURI();
requestURI = StrUtil.subSuf(requestURI, zuulPrefix.length());
requestURI = StrUtil.subSuf(requestURI, requestURI.indexOf("/", 1));
String method = requestContext.getRequest().getMethod();
String permission = method + requestURI;
//第3步:从缓存中获取所有需要进行鉴权的资源(同样是由资源表的method字段值+url字段值拼接成),如果没有获取到则通过Feign调用权限服务获取并放入缓存中
//从缓存中获取所有需要进行鉴权的资源
CacheObject resourceNeed2AuthObject =
cacheChannel.get(CacheKey.RESOURCE,
CacheKey.RESOURCE_NEED_TO_CHECK);
List<String> resourceNeed2Auth =
(List<String>) resourceNeed2AuthObject.getValue();
if(resourceNeed2Auth == null){
//如果没有获取到则通过Feign调用权限服务获取
resourceNeed2Auth = resourceApi.list().getData();
if(resourceNeed2Auth != null){
//并放入缓存中
cacheChannel.set(CacheKey.RESOURCE,
CacheKey.RESOURCE_NEED_TO_CHECK,
resourceNeed2Auth);
}
}
//第4步:判断这些资源是否包含当前请求的权限标识符,如果不包含当前请求的权限标识符,则返回未经授权错误提示
if(resourceNeed2Auth != null){
long count = resourceNeed2Auth.stream().filter((String r) -> {
return permission.startsWith(r);
}).count();
if(count == 0){
//未知请求
errorResponse(ExceptionCode.UNAUTHORIZED.getMsg(),
ExceptionCode.UNAUTHORIZED.getCode(), 200);
return null;
}
}
//第5步:如果包含当前的权限标识符,则从zuul header中取出用户id,根据用户id取出缓存中的用户拥有的权限,如果没有取到则通过Feign调用权限服务获取并放入缓存,判断用户拥有的权限是否包含当前请求的权限标识符
String userId = requestContext.getZuulRequestHeaders().
get(BaseContextConstants.JWT_KEY_USER_ID);
//根据用户id取出缓存中的用户拥有的权限
CacheObject cacheObject = cacheChannel.get(CacheKey.USER_RESOURCE, userId);
List<String> userResource = (List<String>) cacheObject.getValue();
// 如果从缓存获取不到当前用户的资源权限,需要查询数据库获取,然后再放入缓存
if(userResource == null){
ResourceQueryDTO resourceQueryDTO = new ResourceQueryDTO();
resourceQueryDTO.setUserId(new Long(userId));
//通过Feign调用服务,查询当前用户拥有的权限
R<List<Resource>> result = resourceApi.visible(resourceQueryDTO);
if(result.getData() != null){
List<Resource> userResourceList = result.getData();
userResource = userResourceList.stream().map((Resource r) -> {
return r.getMethod() + r.getUrl();
}).collect(Collectors.toList());
cacheChannel.set(CacheKey.USER_RESOURCE,userId,userResource);
}
}
//第6步:如果用户拥有的权限包含当前请求的权限标识符则说明当前用户拥有权限,直接放行
long count = userResource.stream().filter((String r) -> {
return permission.startsWith(r);
}).count();
if(count > 0){
//有访问权限
return null;
}else{
//第7步:如果用户拥有的权限不包含当前请求的权限标识符则说明当前用户没有权限,返回未经授权错误提示
log.warn("用户{}没有访问{}资源的权限",userId,method + requestURI);
errorResponse(ExceptionCode.UNAUTHORIZED.getMsg(),
ExceptionCode.UNAUTHORIZED.getCode(), 200);
}
return null;
}
}
发表回复